Let’s Encrypt is a non-profit certificate authority (CA) that provides free SSL/TLS certificate. Let’s Encrypt allow you to install or request a SSL certificate for free. The SSL/TLS certificate by Let’s Encrypt has 90 days validity and you can renew it anytime also for free.
In this tutorial we will use Certbot to request or obtain a free SSL certificate from Let’s Encrypt.
Certbot is a Let’s Encrypt client that manages Let’s Encrypt SSL certificates. A fully-featured Let’s Encrypt client that can automate task, obtaining, and renewing SSL certificates.
Let’s proceed with the steps on how to secure our website with Let’s Encrypt.
Prerequisites
Let’s Encrypt SSL/TLS certificate can only be installed on a server with a registered domain name. You need to make sure that your Domain A record is pointed to your server because Let’s Encrypt needs to validate the domain if it is properly pointed to the server where you request to obtain the SSL certificate.
Installing Certbot
In this section we will guide you on how to install Certbot with Apache and Nginx Webserver.
For Apache web server.
sudo apt install certbot python3-certbot-apacheFor Nginx web server.
sudo apt install certbot python3-certbot-nginxGenerating the SSL Certificate
For Apache web server.
sudo certbot --apacheAfter initiating the command follow the instruction below.
Output:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): [email protected]- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: domain.com
2: www.domain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1,2We selected 1 and 2 for the www subdomain to be included in the SSL certificates.
Note: You can opt if you don’t want to include the www subdomain, just select 1 and press enter.
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel):2
Redirecting vhost in /etc/apache2/sites-enabled/domain.com.conf to ssl vhost in /etc/apache2/sites-available/domain.com-le-ssl.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations! You have successfully enabled https://domain.com
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=domain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/domain.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/domain.com/privkey.pem
Your cert will expire on 2022-03-05. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
For Nginx Web server.
sudo certbot --nginxOUTPUT:
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): [email protected]
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Account registered.
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: domain.com
2: www.domain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1,2
Requesting a certificate for domain.com
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/domain.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/domain.com/privkey.pem
This certificate expires on 2022-07-28.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
Deploying certificate
Successfully deployed certificate for domain.com to /etc/nginx/sites-enabled/domain.com.conf
Congratulations! You have successfully enabled HTTPS on https://domain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -That’s it congratulation!
Test the SSL certificate
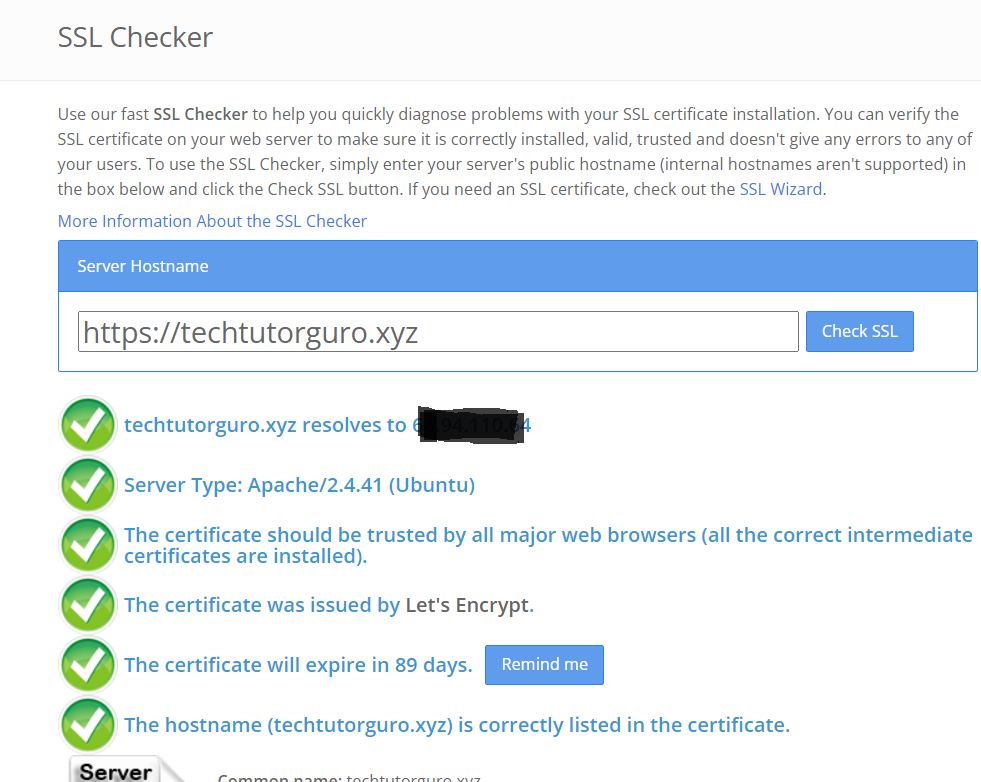
After the installation you can verify if the SSL certificate is installed on your website by just accessing it with https://domain.com. You can also verify it by using an SSL Checker webiste like https://www.sslshopper.com/ssl-checker.html.
SSL Certificate Renewal
When you install Certbot it will automatically setup a auto renewal script since Let’s Encrypt is only valid within 90 days or 3 months. To check if the auto renewal script is running, run this command.
systemctl status certbot.timer● certbot.timer - Run certbot twice daily
Loaded: loaded (/lib/systemd/system/certbot.timer; enabled; vendor preset: enabled)
Active: active (waiting) since Sun 2021-12-05 13:33:10 EST; 45min ago
Trigger: Mon 2021-12-06 00:10:45 EST; 9h left
Triggers: ● certbot.service
Dec 05 13:33:10 domain.com systemd[1]: Started Run certbot twice daily.The Certbot timer will run twice a day to check if there are domains that ready for renewal.
There are cases that Certbot timer fails to renew the domains on time that causes the certificates to expires. In this case you can manually renew the domains by running this command.
sudo certbot renewYou can also do a renewal dry run to test if the SSL renewal is working as expected. To do that run this command.
sudo certbot renew --dry-runConclusion
We have demonstrated how to secure our sites using Let’s Encrypt SSL certificate. In this tutorial you also able to learned how to use Certbot to renew and obtain a free Let’s Encrypt SSL certificate.
If you want to learn more about on how to secure your server you can check fail2ban tutorial.
If you have questions, feel free to leave a comment and we will try to answer it.
Thank you and hope you enjoy our tutorial ?





